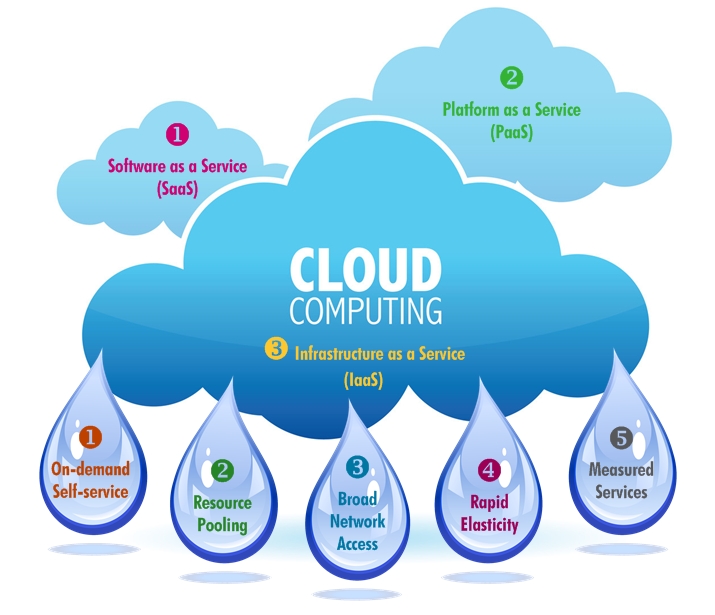
Software as a Service (SaaS) is now evolving as the strategy for overcoming most talked recession. More and more companies are now changing to SaaS marketing based applications from on premise applications and more and more companies are now offering their products/services in SaaS model.

Software as a Service is still in its early days and even now contributing to success of most small and medium sized businesses (SMBs). Compared to on-premise or traditional business applications and technologies, SaaS holds many advantages; it is cheap, easy to implement, has higher user adoption rates, has web based interface, global accessibility, easy to go wireless, easy to customize, no cost for maintenance, minimum need of technical knowledge, no in-house data warehousing requirements, no need for updates or additional purchases, open-source nature (not for all), per user fee schedule, advanced contact and data sharing tools, easy integration with existing systems, and so on.
For small and medium sized businesses having lesser number of employees (application users), SaaS offer an excellent opportunity; because they get most sophisticated system for lowest costs. As said earlier, SaaS is still in its early days, and now only a few types of SaaS applications are available for commercial purposes. Most promising SaaS marketing applications for SMBs include:
1. Customer Relationship Management (CRM) applications – They help you to automate and manage all or most of your business practices including customer service, product sales, after sale service, contact management, account management, event scheduling, analytics, etc. CRM systems are the most popular and widely adopted SaaS applications.
2. Web conferencing applications – SaaS based web conferencing has revolutionized the whole world of web conferencing. Now companies/persons can share and present documents, power-points, graphics, whiteboards without the need of a server, software installation and supporting technical staff. The same can be noted with VoIP and PBX systems.
3. Sales Force Automation (SFA) systems – These are on demand systems for enhancing co-operation between sales peoples by providing them proper communication, analysis, scheduling and data sharing tools. There are independent SFA systems and SFA systems integrated with CRM systems.
4. Contact management (email) applications – These are business applications for storing customer and employee details and communicating with them with the help of an e-mail client, usually MS Outlook. Like SFA systems, contact management applications may either independent or integrated with CRM or SFA systems.
5. Document management and data backup applications – for storing and sharing data related to company, products, customers, etc. in a remote place secured from most data disasters.
All or most of the above applications were once available only to large enterprises because of the cost involved in developing them and implementing them. But now with SaaS applications SMBs can compete with these large enterprises by subscribing to applications which often outperform big business applications. But Software as a Service is not that much a perfect solution. The main concern is data security, as you are sharing your precious business data with a second person over. Many large and medium sized businesses are avoiding SaaS applications because of the above reason but a lot has been done to improve on that.